The silent breach: Why proactive cyber resilience is everything
Worried about data breaches? Learn how to spot threats early and keep your business protected.
-
Editorial Team
- September 26, 2025
- 4 minutes

The financial services industry is in a state of constant change, and with that evolution comes an ever-growing array of cyber threats. While the industry has long focused on robust defenses, today’s attackers are more sophisticated, often bypassing traditional security measures. This is why a proactive approach, one that focuses on identifying and mitigating threats before they escalate into full-blown breaches, is no longer a luxury, but a necessity.
A data breach can be a silent affair in its early stages, but its consequences are anything but. According to IBM, it takes a staggering
292 days on average to detect and contain breaches involving stolen credentials. That’s nearly a year where an attacker can operate undetected, exfiltrating sensitive data and causing irreparable harm. The financial implications alone are severe, with the global average cost of a breach in 2024 hitting an estimated
$4.88 million. Beyond the financial fallout, a breach erodes customer trust, damages brand reputation, and can lead to significant legal and regulatory penalties.
The Anatomy of a Breach: Common Attack Vectors
Understanding how breaches happen is the first step to preventing them. They are not always the result of a single, catastrophic failure, but often a combination of vulnerabilities that attackers exploit. In the financial sector, where a single weak link can expose millions of customer records, the risk is particularly high.
Some of the most common ways attackers gain access include:
- Social Engineering and Phishing: Manipulating employees into revealing credentials or clicking malicious links remains a primary attack vector.
- Weak Credentials: Stolen or easily guessable passwords are a frequent entry point, especially when not protected by multi-factor authentication (MFA).
- Third-Party Vulnerabilities: The interconnected nature of fintech means a security gap in a vendor’s system can become a gateway for an attacker to compromise your network.
- Unpatched Software: Outdated systems with known security holes are an open invitation for cybercriminals to gain a foothold.

Beyond the Headlines: The Case for Continuous Monitoring
The traditional model of waiting for a security alert to signal a breach is no longer sufficient. By the time an alert is triggered, an attacker may have already moved laterally across the network and compromised critical systems. This is why security leaders are shifting their focus to continuous, proactive threat exposure management.
Continuous monitoring involves more than just internal network scanning. It includes actively looking for signs of compromise on external sources, such as:
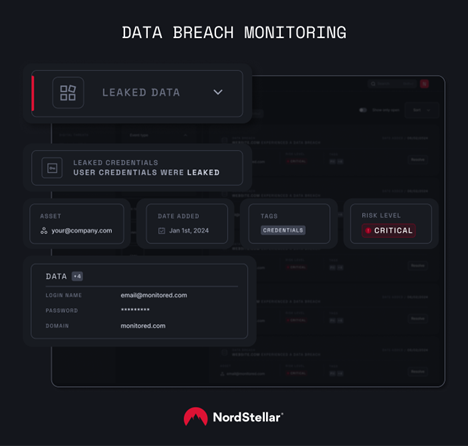
- The Deep and Dark Web: Monitoring for exposed company credentials, stolen data, or discussions about planned attacks can provide an early warning. NordStellar, for example, scans over 25,000 sources, including hacker forums and underground markets, for keywords related to your organization.
- Compromised Accounts: Real-time alerts on stolen login details, including session cookies, can prevent account takeovers before they occur. The platform monitors for compromised credentials and can be integrated to block leaked passwords.
- Proactive Vulnerability Checks: The platform also uses password fuzzing to catch predictable variations of exposed passwords, preventing attackers who rely on guesswork.
This approach gives security teams a strategic advantage. Instead of a post-mortem analysis, they get a real-time, actionable view of their external risk posture. It allows them to prioritize and remediate the most critical issues before they can be leveraged to cause damage.
Building Your Shield: Essential Pillars of Prevention
While advanced monitoring tools are crucial, they are most effective when combined with foundational security practices. For CISOs and security professionals in the financial industry, a layered defense strategy is essential.
- Robust Authentication: Implement MFA across all systems, especially for privileged accounts, to significantly reduce the risk of credential-based attacks.
- Principle of Least Privilege: Give employees only the permissions they need to do their jobs, limiting the potential damage from a compromised account.
- Employee Security Training: The human element remains a significant vulnerability. Regular, engaging training can empower employees to become the first line of defense against social engineering and phishing attempts.
- Secure Coding Practices: Encrypt sensitive data to protect it even if it’s stolen. Keep software updated with the latest security patches.
- Vendor Risk Management: Establish a clear framework for assessing and continuously monitoring the security posture of all third-party vendors and partners.
By combining proactive threat intelligence with a strong security culture and foundational best practices, financial institutions can build a resilient defense that stays one step ahead of the threat.


 Bobsguide is a
Bobsguide is a